THE HACKER NEWS

swolpers
2 hours ago
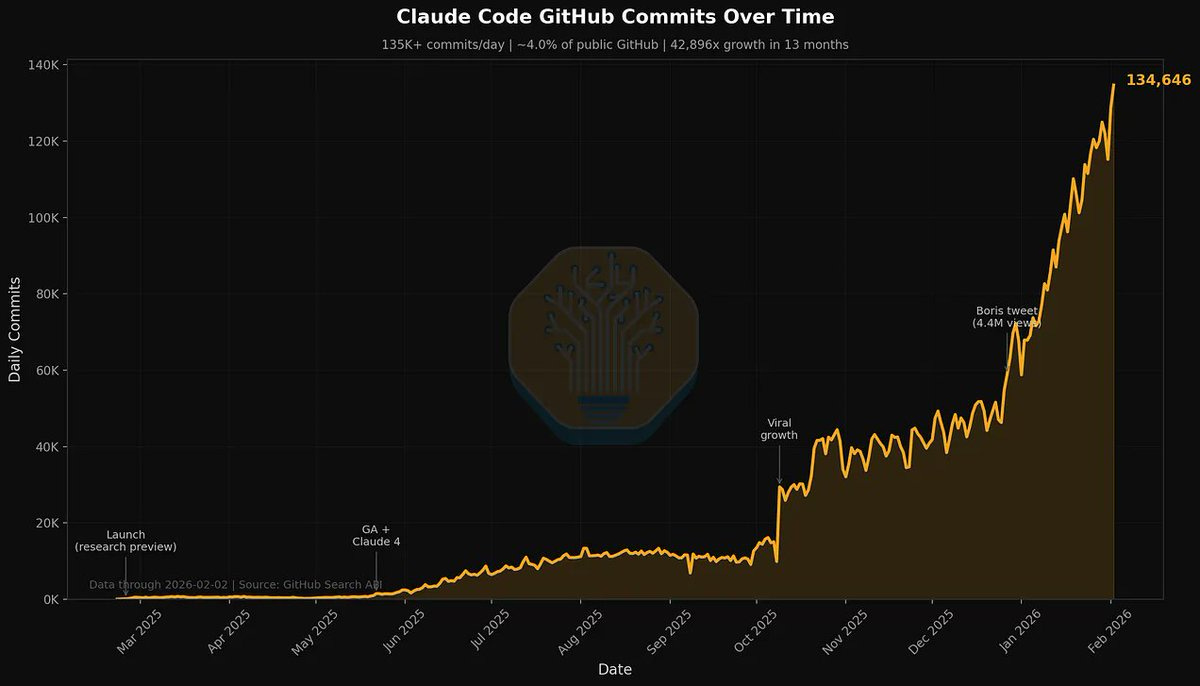
Claude Code, Claude Cowork and Codex #5
It feels good to get back to some of the fun stuff. The comments here can double as a place for GPT-5.4 reactions, in addition to my Twitter thread. I hope to get that review out soon. Almos...
11 HOURS AGO
SPENVO
OpenAI is walking away from expanding its Stargate data center with Oracle
14 HOURS AGO
1970-01-01
Florida judge rules red light camera tickets are unconstitutional
21 HOURS AGO
ROBIN_REALA
Ireland shuts last coal plant, becomes 15th coal-free country in Europe (2025)
15 HOURS AGO
TAMBOURINE_MAN
I don't know Apple's endgame for the Fn/Globe key–or if Apple does
A DAY AGO
SUDHAKARAN88
FFmpeg at Meta: Media Processing at Scale
3 DAYS AGO
ZDW
The window chrome of our discontent
4 DAYS AGO
RUNNINGMIKE
Unlocking Python's Cores:Energy Implications of Removing the GIL

philippemnoel
a day ago
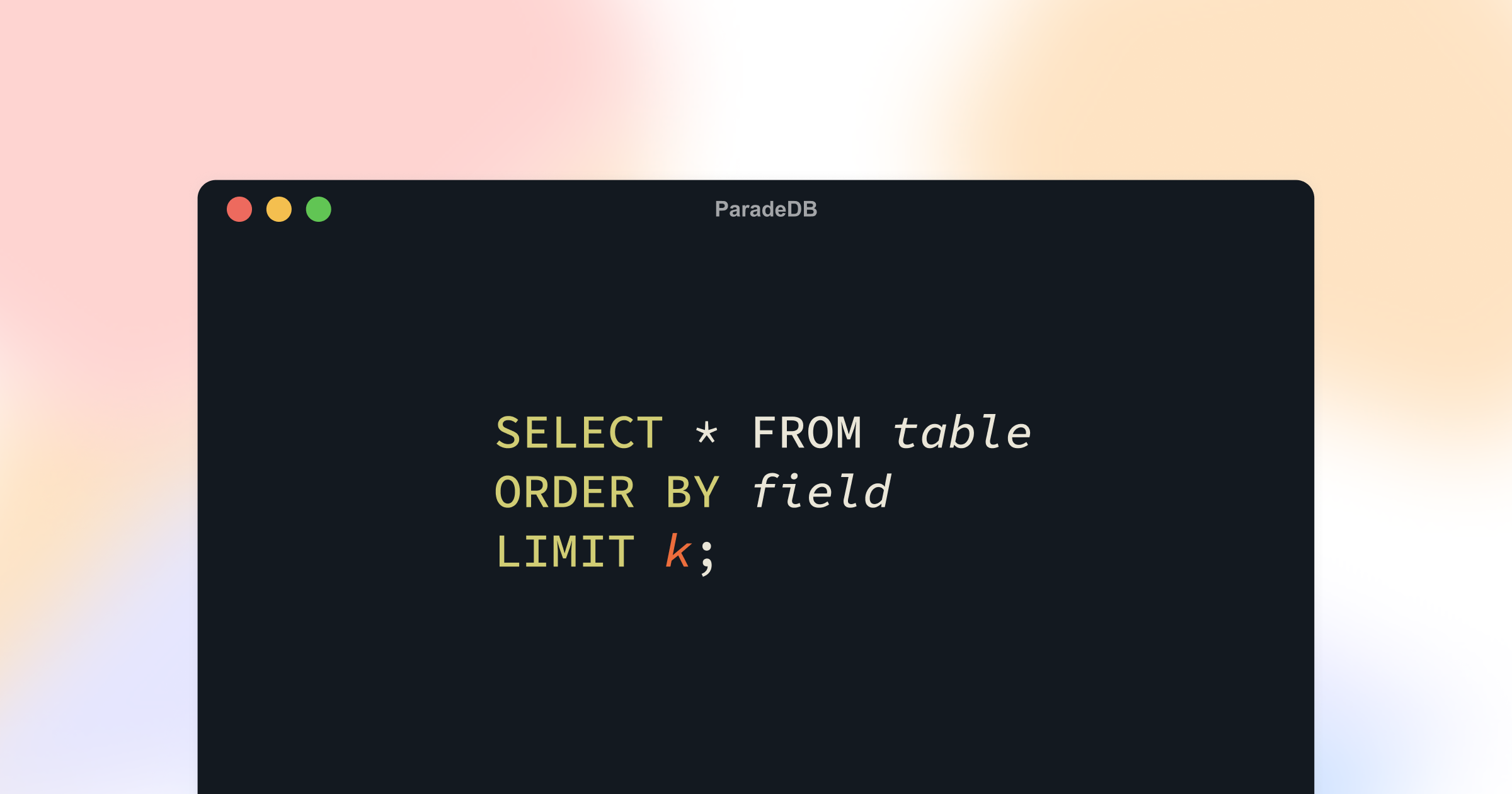
Optimizing Top K in Postgres
How ParadeDB uses principles from search engines to optimize Postgres' Top K performance.

jenthoven
5 hours ago
Learnings from paying artists royalties for AI-generated art
A retrospective on Tess.Design, our attempt to make an ethical, artist-friendly AI marketplace. We launched Tess in May 2024 and shut it down in January 2026....

jhalderm
7 hours ago
The “JVG algorithm” only wins on tiny numbers
Sorry to interrupt your regular programming about the AI apocalypse, etc., and return to the traditional beat of this blog’s very earliest years … but I’ve now gotten multiple mes…...

kumar_abhirup
17 hours ago
Show HN: DenchClaw – Local CRM on Top of OpenClaw
Fully Managed OpenClaw Framework for all knowledge work ever. CRM Automation and Outreach agents. The only local productivity tool you need. - DenchHQ/DenchClaw...

jnord
8 hours ago
No, it doesn't cost Anthropic $5k per Claude Code user
The viral claim that Anthropic loses $5,000 per Claude Code subscriber doesn't survive basic scrutiny. Let's do the actual maths....


dolin_ch
4 days ago
A useless infinite scroll experiment
A weird and useless website to waste time. An absurd experiment in endless scrolling where the void slowly wins. How far will you go?...


petethomas
2 hours ago
Amazon holds engineering meeting following AI-related outages
Ecommerce giant says there has been a ‘trend of incidents’ linked to ‘Gen-AI assisted changes’...


TMWNN
4 days ago
Lotus 1-2-3 on the PC with DOS
VisiCalc started it, but 1-2-3 finished it. "It" being the discussion of what a spreadsheet can be, and also VisiCalc itself....
 https://stonetools.ghost.io/lotus123-dos/
https://stonetools.ghost.io/lotus123-dos/
mitchbob
12 hours ago
Notes on Baking at the South Pole
Notes on baking at the South Pole....

kjellsbells
3 hours ago
Windows: Microsoft broke the only thing that mattered
Any tech nerd knows the unspoken contract that comes with being the only tech-literate person in the family. You get texts when someone's laptop is slow, called over during the holidays to f...

baconomatic
19 hours ago
Reverse-engineering the UniFi inform protocol
Every UniFi device phones home to its controller on port 8080. The payload is AES-encrypted, but the header is plaintext, and that's enough to build multi-tenant routing....

owlstuffing
2 days ago
Rethinking Syntax: Binding by Adjacency
Manifold is a Java compiler plugin, its features include Metaprogramming, Properties, Extension Methods, Operator Overloading, Templates, a Preprocessor, and more. - manifold-systems/manifol...

anigbrowl
12 hours ago
Gabibi is a tool for intentionally degrading images (in Japanese)
画像をあえてガビガビに劣化させるツール。解像度リサイズとJPEG再帰圧縮で、デジタル特有の不完全さを再現します。...

dmonterocrespo
2 days ago
Velxio, Arduino Emulator
Write, compile, and simulate Arduino sketches entirely in your browser. Real AVR8 CPU at 16 MHz, 48+ electronic components, Serial Monitor, and Library Manager. Free & open source....
 7:34:33 AM TUESDAY MARCH 10, 2026
7:34:33 AM TUESDAY MARCH 10, 2026