THE HACKER NEWS

jhalderm
4 hours ago
The “JVG algorithm” only wins on tiny numbers
Sorry to interrupt your regular programming about the AI apocalypse, etc., and return to the traditional beat of this blog’s very earliest years … but I’ve now gotten multiple mes…...
5 HOURS AGO
JNORD
No, it doesn't cost Anthropic $5k per Claude Code user
2 DAYS AGO
DMONTEROCRESPO
Velxio, Arduino Emulator
A DAY AGO
SUDHAKARAN88
FFmpeg at Meta: Media Processing at Scale
4 DAYS AGO
RUNNINGMIKE
Unlocking Python's Cores:Energy Implications of Removing the GIL
2 DAYS AGO
NANNA
Segagaga Has Been Translated into English

jenthoven
2 hours ago
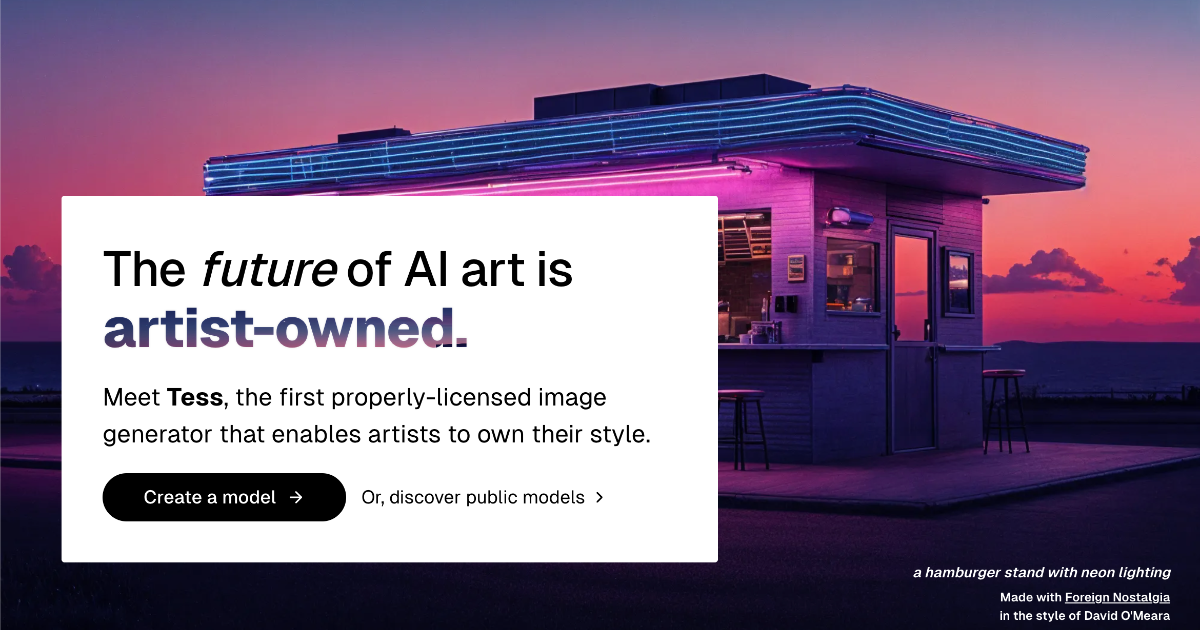
Learnings from paying artists royalties for AI-generated art
A retrospective on Tess.Design, our attempt to make an ethical, artist-friendly AI marketplace. We launched Tess in May 2024 and shut it down in January 2026.

1970-01-01
11 hours ago
Florida judge rules red light camera tickets are unconstitutional
A Broward County judge has dismissed a red-light camera ticket....


ratwolf
4 days ago
Show HN: Hopalong Attractor. An old classic with a new perspective in 3D
Generative Density Approximation for Deterministic Chaos The Hopalong Attractor - ratwolfzero/hopalong_python...

mitchbob
9 hours ago
Notes on Baking at the South Pole
Notes on baking at the South Pole....


spenvo
8 hours ago
OpenAI is walking away from expanding its Stargate data center with Oracle
The OpenAI deal fallout exposes the fundamental danger of being the most leveraged player in a market where the chip cycle moves faster than the concrete dries....


tambourine_man
12 hours ago
I don't know Apple's endgame for the Fn/Globe key–or if Apple does
The origin and the evolution of the most confusing modifier key...


robin_reala
18 hours ago
Ireland shuts last coal plant, becomes 15th coal-free country in Europe (2025)
Moneypoint in County Clare, Ireland, joins the ranks of other European nations exiting coal by shutting off power generation at its sole remaining coal plant. Industry observers say Ireland’...


kumar_abhirup
14 hours ago
Show HN: DenchClaw – Local CRM on Top of OpenClaw
Fully Managed OpenClaw Framework for all knowledge work ever. CRM Automation and Outreach agents. The only local productivity tool you need. - DenchHQ/DenchClaw...

owlstuffing
2 days ago
Rethinking Syntax: Binding by Adjacency
Manifold is a Java compiler plugin, its features include Metaprogramming, Properties, Extension Methods, Operator Overloading, Templates, a Preprocessor, and more. - manifold-systems/manifol...

anigbrowl
9 hours ago
Gabibi is a tool for intentionally degrading images (in Japanese)
画像をあえてガビガビに劣化させるツール。解像度リサイズとJPEG再帰圧縮で、デジタル特有の不完全さを再現します。...

zdw
3 days ago
The window chrome of our discontent
In a WWDC 2011 session, Dan Schimpf explained some of the goals of the refreshed design for Aqua in Mac OS X Lion were “meant to focus the user attention on the active window content”. This ...

rendx
19 hours ago
FontCrafter: Turn your handwriting into a real font
Convert your scanned handwriting into custom OTF, TTF, and WOFF2 fonts with local browser processing and vectorization. No account or uploads needed....
 4:35:11 AM TUESDAY MARCH 10, 2026
4:35:11 AM TUESDAY MARCH 10, 2026